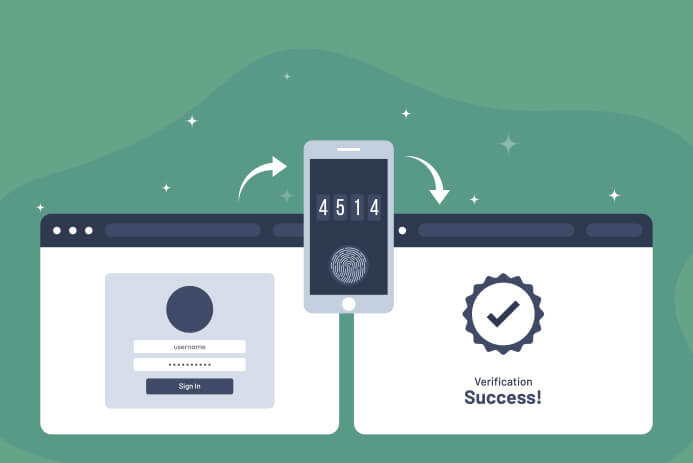
3 reasons why MFA needs to be a part of your remote access strategy
Like every other business, when the pandemic hit, your IT department hurried to find a way to enable a now-remote workforce to access their work machines and/or the corporate network from home.