Using remote access software involves opening up a path to your information and potentially exposing sensitive data, which is why any solutions that can remotely access your organization’s files must pass stringent cyber security measures.
That’s why in this guide, we’ll explore:
- TeamViewer’s security protocols and how they work to protect your company’s assets
- Teamviewer security breaches and any other security risks you should be aware of
- Step-by-step actions to maximize safety while using remote access tools
- A top TeamViewer alternative for your remote access needs
Let’s have an objective look at TeamViewer, learn about its security features, and assess whether it’s the right choice for keeping your workplace secure.
Overview of TeamViewer's Security Features
At its core, security for TeamViewer consists of two main areas: ensuring authorized access and preventing unauthorized attempts.
1. Two-factor authentication (2FA)
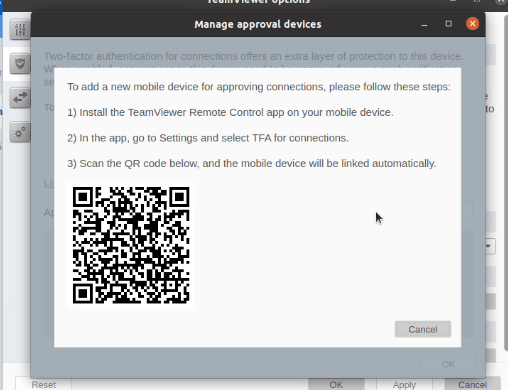
Firstly, two-factor authentication (2FA) adds an extra layer of security, requiring a second form of verification beyond just a password. Biometric protection further enhances this with fingerprint or face recognition on compatible devices to give access permission.
2. Brute-force protection
If someone tries guessing your password, TeamViewer doesn’t make it easy. After each failed attempt, the wait time for the next try gets longer. With delays exponentially increasing, it would take an attacker around 17 hours to make just 24 attempts.
3. Custom black screen

For visual security needs, the custom black screen allows you to display a pre-designed image on the remote screen.
4. Password protection

Another layer of precaution is the option to protect your TeamViewer options (your personal Teamviewer’s settings) with a strong password.
Pro tip from RealVNC: generate unique strong passwords for each app and tool you’re using, then store them with a password manager. This way, you can decrease security risk without having to memorize crazy and complicated credentials.
5. Encryption
Of course, encryption is crucial for any remote access tool. It’s designed to make breaches incredibly difficult and deny access from unsafe devices, which is crucial in a landscape where cyber threats are continuously on the rise.
6. Teamviewer fingerprint
Every device equipped with TeamViewer has a distinct fingerprint––a sequence composed of letters, numbers, and special characters, generated from the device’s public key. On top of this feature, TeamViewer uses ‘expert identity,’ helping you ensure that the session request comes from the person you expect to connect your TeamViewer account with.
Encryption Methods

Is TeamViewer safe? Let’s see. TeamViewer uses encryption protocols that are applied to all data traveling through their network, which safeguards the content of remote sessions from unauthorized access.
Here’s a closer look at their encryption protocols:
- RSA 4096-bit Key Exchange: This creates a secure channel for the subsequent exchange of session data, and since the private key never leaves the host machine, interception seems impossible.
- AES 256-bit Session Encryption: This is the industry standard for secure communications and is widely regarded as solid enough to protect sensitive data against brute-force attacks and other decryption attempts.
- Perfect Forward Secrecy: PFS means that even if a key from one session were to be compromised, it would not affect the security of other sessions since they have different keys.
Authentication Methods for the Teamviewer Account
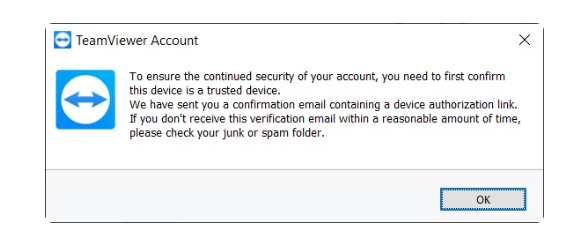
Authentication methods in TeamViewer accounts are created to ensure that only verified users gain access:
- In the case of a new session logging from unregistered devices, TeamViewer requires device authorization via email to confirm the new device before it can be used to gain TeamViewer access.
- Two-factor authentication uses a code generated by a mobile authentication app, in addition to the standard password.
- The TeamViewer software includes data integrity checks to ensure that the data received has not been altered during transmission to prevent man-in-the-middle attacks.
Compliance with Industry Standards
TeamViewer is compliant with the following industry standards and regulations:
- ISO/IEC 27001: It ensures that a company has established and follows a systematic approach to managing sensitive information.
- ISO 9001: This guarantees that they maintain high consistency in delivering services that meet customer and regulatory requirements.
- General Data Protection Regulation (GDPR): GDPR rules require strict handling and protection of personal data for EU residents.
- SCC (Standard Contractual Clauses): These are used for legal data transfer outside the EU.
- Health Insurance Portability and Accountability Act (HIPAA) Hi-Tech: Crucial for clients in the healthcare industry dealing with protected health information (PHI).
- Service Organization Control (SOC) 2 Type II/SOC 3: These reports indicate that TeamViewer manages customer data based on the pillars of security, availability, processing integrity, confidentiality, and privacy.
- Trusted Information Security Assessment Exchange (TISAX): Meaning that TeamViewer is compliant with automotive industry-specific security standards.
- PCI DSS (Payment Card Industry Data Security Standard): Important for companies that handle credit card transactions and maintain a secure payment environment.
Examining TeamViewer's Security Vulnerabilities

- One of the primary security concerns with TeamViewer is unauthorized access. There have been reports of attackers exploiting weak or reused passwords to gain control over users’ computers.
- Another vulnerability relates to Man-in-the-Middle (MiTM) attacks. TeamViewer has implemented solid protocols to prevent MiTM attacks, such as end-to-end encryption. Despite these measures, we don’t recommend using TeamViewer on unsecured or public networks.
- Delays in software updates can leave your systems vulnerable.
- Sometimes, vulnerabilities like external password breaches come from user behavior.
What’s more––TeamViewer, like any software, can face zero-day exploits, which are unknown to them until attackers exploit the TeamViewer app.
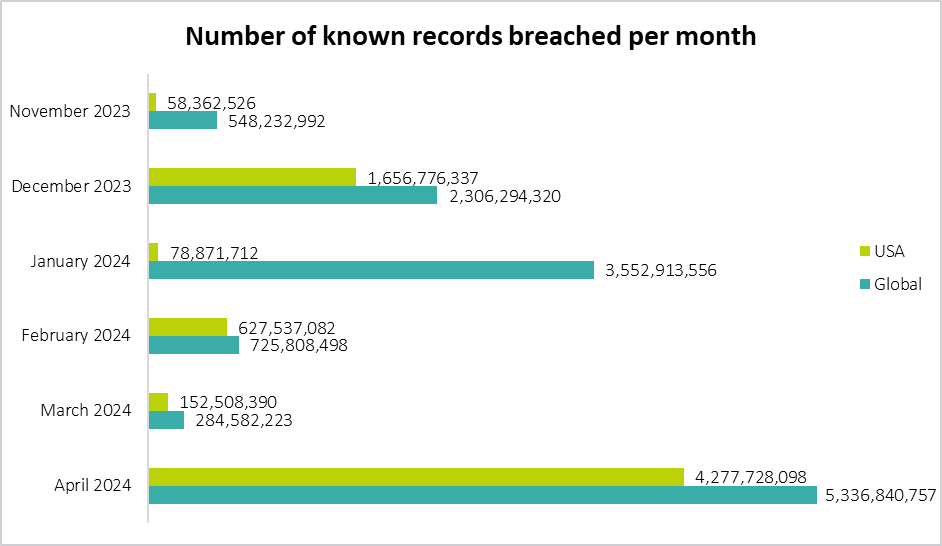
History of Teamviewer Security Breaches and Vulnerabilities
So far, Teamviewer looks like a safe choice for your business. However, upon a closer look, it seems that even with such advanced security features, users reported security breaches after using the software.
- One of the most prominent security concerns occurred in 2016 when TeamViewer confirmed that Chinese hackers managed to breach its system.
- Moreover, there were reports of other incidents where hackers exploited TeamViewer to install ransomware or access sensitive data.
- In January 2024, a breach allowed attackers to deploy ransomware via TeamViewer.
So, is Teamviewer safe? It depends on how you use it. As a response to growing cyber threats, the company stated: “Our analysis shows that most instances of unauthorized access involve a weakening of TeamViewer’s default security settings. This often includes the use of easily guessable passwords which is only possible by using an outdated version of our product.”
Common Attack Vectors and Risks

Although it’s a popular remote access solution with advanced security options, TeamViewer opens up a series of common attack vectors the moment you press ‘install software,’ and here’s why:
- Attackers can use deceptive emails to trick users into disclosing their login credentials, which has happened before with multiple sites.
- Credential stuffing is also a major issue. This involves using known username and password combinations obtained from other data breaches to access TeamViewer accounts.
- TeamViewer, like all software, encounters flaws that can be exploited if you don’t update your app regularly (both the desktop version and on your mobile device).
The Importance of Evaluating Remote Access Security
Unfortunately, remote access tools are a potential entry point for cyberattacks. That’s why you must evaluate them thoroughly before entrusting your organization (or non-commercial users) with these tools. Below, we’ll dive into a checklist for assessing remote support software.
Assessing the security of remote access solutions
- Review security features: Examine encryption standards, multi-factor authentication (MFA), and the strength of password policies.
- Monitor regular updates and patch management: Does your software offer regular updates that address vulnerabilities?
- Check their certifications: Check for compliance with industry standards and regulations, such as GDPR, ISO/IEC 27001, or ISO 9001.
- Test the access control and user management: Evaluate the granularity of access controls, and if user management allows for role-based access controls, multiple permission settings, and activity logging monitoring based on IP addresses.
- Penetration testing and vulnerability scans: Do they employ regular penetration testing and vulnerability scans conducted by independent third parties?
- Vendor reputation: Examine their history with security incidents and their response. Look at the level of support provided and independent user reviews.
- Architecture and infrastructure: For example, cloud-based solutions need strong security measures for data storage and transmission. For on-premises solutions, examine how the software integrates with existing corporate firewalls.
A Safe Alternative To Teamviewer: RealVNC Connect
RealVNC Connect is tailored for those who place a premium on digital safety and seek a secure, dependable remote access solution. The company created an environment where flexibility in access does not compromise on supreme security. Let’s explore why RealVNC is a solid alternative to TeamViewer.
"RealVNC® makes it really easy for me, from virtually anywhere, to use my phone or tablet to look into and fix a problem should something arise."
Matt Ireland, Founder, MiPi Support
RealVNC's security features
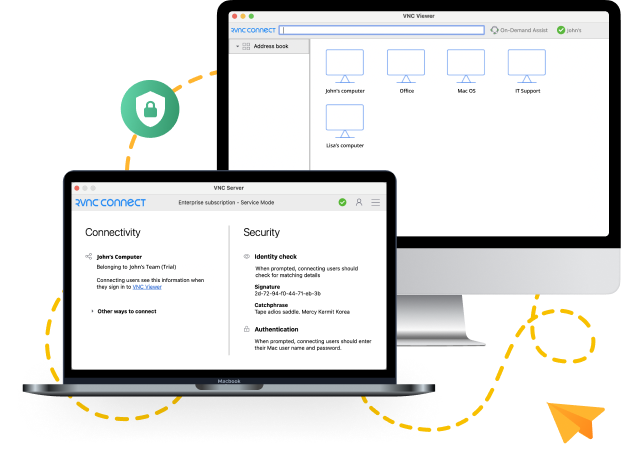
- RealVNC does not retain session data, so it cannot be decrypted now or in the future—securing your information against retrospective breaches.
- Each connection assumes a hostile context, suggesting an always-on defensive shield.
- The remote computer ultimately dictates the terms of connection, putting the power in the hands of the legitimate user for strict access control.
- End-to-end encryption is a non-negotiable feature, with up to 256-bit AES ensuring data is protected across all connections, whether via VNC Cloud or over a LAN.
- The integrity of endpoints is verified using 2048-bit RSA keys, guarding against Man-in-the-Middle (MITM) attacks.
- All communications employ HTTPS.
- RealVNC uses multi-factor authentication (MFA), single sign-on (SSO), and network access control.
- Endpoint security is also a top feature of RealVNC, protecting individual devices from cyber threats.
Flexible deployment options
RealVNC Connect accommodates a wide range of IT environments. You can choose between on-premise and cloud-based setups with this remote access software.
- For organizations that require the utmost security, RealVNC offers an on-premise deployment option with offline licensing.
- On top of this, RealVNC provides cloud solutions and direct connectivity. This way, you can employ internet-powered access and direct connections for devices that need to remain isolated.
- What’s more, IT teams can implement custom automations and integrations through RealVNC’s APIs.
Commitment to data protection
RealVNC offers best-in-class security practices by subjecting its services to third-party security audits, including white box security evaluations. On top of the ISO 27001 certification, this remote support solution also adheres to GDPR standards and is HIPAA and PCI-DSS-compliant, offering a range of other sector-specific regulations.
Partner with RealVNC––the Leading Remote Access Software on the Market
Given the massive shift in remote work and the evolving workforce migration, organizations must train and monitor employees to mitigate these cyber risks, while also ensuring that past team members’ activities don’t become liabilities. And with hackers constantly in search of system vulnerabilities, you need the best protection on the market to keep your data secure.
So, in this context, is TeamViewer safe for professional use? The answer is…nuanced. TeamViewer can be considered secure, provided that users are diligent with its application. This includes regular updates, proper usage protocols, and a reliance on the provider to address vulnerabilities on time.
But before you consider TeamViewer, here’s a better alternative: RealVNC—a more polished and sophisticated remote access option.
RealVNC complies with the most rigorous industry standards while offering remote access tools that boost remote work capabilities and organizational security. Don’t believe us? Get your free trial today and try it out for yourself.





