Given the remote working landscape (including the rising popularity of BYOD policies) and ever-rising cyber threats, remote access software is one of the most critical components of our work environment. One name that often pops up in this field is Splashtop. But, is Splashtop safe?
The short answer is Splashtop has met the relevant security requirements for various accreditations, but that comes with all the usual qualifications that any online service needs- no system is entirely foolproof after all.
When you’re dealing with tools that bridge sensitive data and systems, it pays to do your research. For this reason, we’re diving deep into the safety and security protocols surrounding Splashtop (and remote-access platforms in general), offering the 360-degree analysis you need to make an informed decision without spending hours on research.
In this guide, we’ll will cover:
- Risks and vulnerabilities inherent with remote access technology
- Splashtop’s overall review
- Examination of Splashtop’s security protocols
And so much more! Let’s get started.
Why Remote Access Security Matters
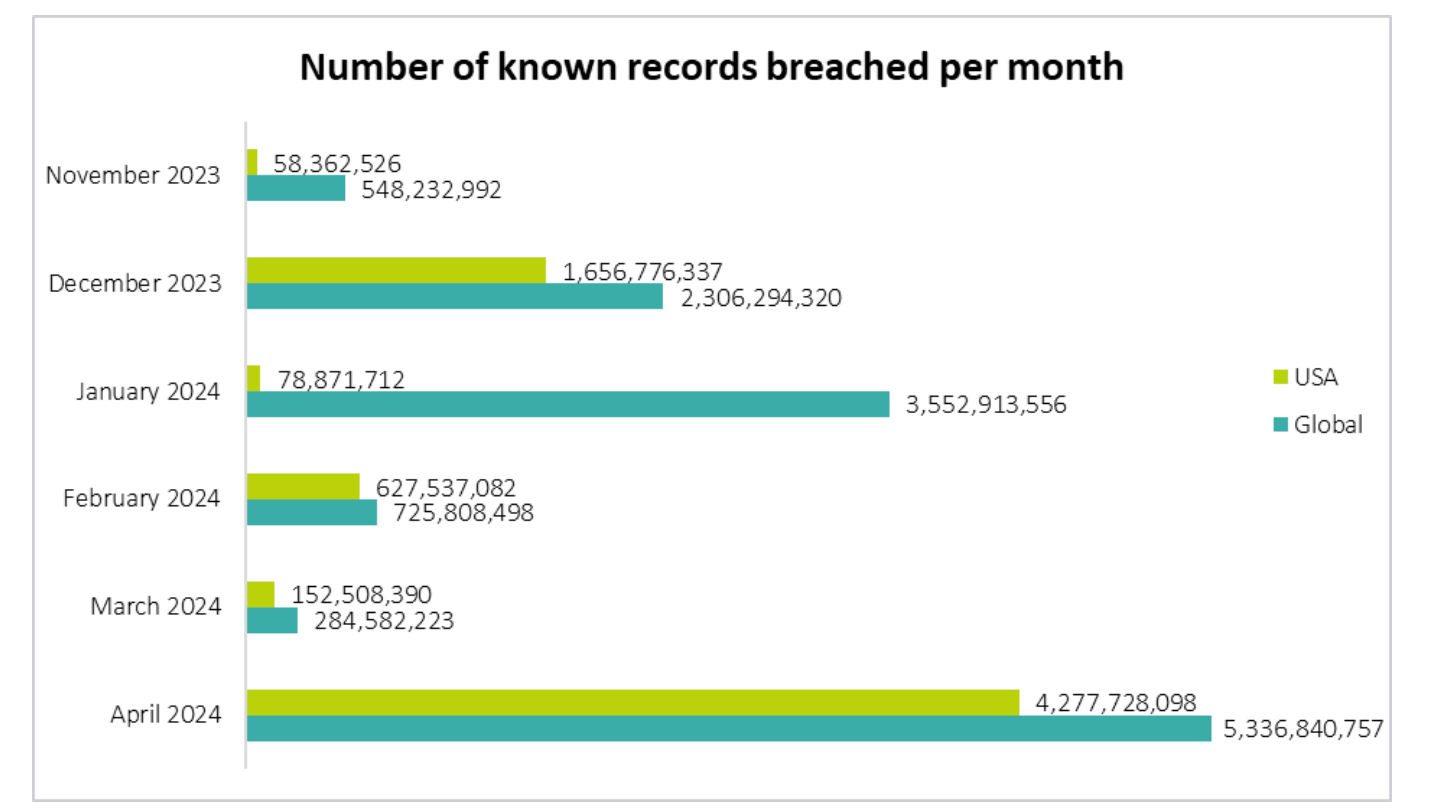
The number of cyberattacks leading to data breaches has dramatically increased over the past years. And it looks set to continue increasing.
Which is why security matters for every technology we use at home or in the workplace.
This is why RealVNC is determined to provide the most secure remote access solution on the market.
In our opinion, when investigating the security of remote access solutions, you should go beyond the surface features and weigh up aspects like access policies, user activity monitoring, endpoint security for desktop and mobile access, and more.
The deeper you dive into this research, the more confident you should feel in your choices. If you find that, rather than reassurance, you have more questions than you began with, it might be worth considering other options.
After all, being able to entrust your sensitive data with a remote access solution is one crucial aspect of your cybersecurity strategy, which isn’t just ‘nice to have’. Given the current online security landscape, it’s a must.
Assessing the Security of Remote Access Solutions
When evaluating remote access tools, consider the following key components to ensure top-level security:
1. Examine the access policies
Policies should define who can access what resources, under what conditions, and mandate strong password practices.
Multi-factor authentication (MFA) is non-negotiable for secure remote access. It adds an extra layer of security that mitigates the risk of unauthorized access to your office computer.
Access policies should align with regulatory standards like ISO 27001 and GDPR. These standards ensure your remote desktop access complies with best practices in security and privacy.
Other must-have features include:
- Detailed logging of remote sessions and user activity
- Role-based access controls
- Integration with SSO
2. Scan for vulnerabilities
Look for previous vulnerabilities and how the vendor has managed past security incidents to understand their commitment to security. Regularly scan both the remote access software and the endpoint devices for vulnerabilities. Use tools like Nessus or OpenVAS to identify potential security risks.
Look for vendors with a robust history of managing past vulnerabilities and security issues transparently. Ensure your chosen solution provides automatic updates to patch new vulnerabilities, cutting out the risk of a simple error from your IT department leading to disaster.
3. Monitor user activity
Your remote support solution must be able to monitor and log user activities during remote sessions, whether on desktop or mobile devices. This includes capturing login attempts, session durations, and actions performed during access.
Tools like RealVNC can monitor all these activities, and set up real-time alerts to quickly respond to suspicious activities.
Detailed audit logs also help track and monitor access activities, providing a clear audit trail for security reviews. Make sure your remote support software provides this feature and that the audit logs can be easily exported and analyzed.
4. Consider encryption strength
Evaluate the encryption protocols used by the remote access tool. Ensure that the solution employs strong encryption mechanisms such as AES-256 and TLS (including TLS 1.2 or higher). Confirm that encryption is end-to-end to protect data from interception and unauthorized access during transit.
5. Authentication mechanisms
Popular authentication mechanisms like two-factor authentication (2FA) and single sign-on (SSO) should be available. Support for device authentication ensures that only authorized devices can access the network.
Did you know that RealVNC uses MFA, SSO, and network access control to manage authentication for remote users?
6. Review security protocols
Which security protocols does the remote access solution follow? This question is crucial, as protocols such as the ISO 27001 certification, GDPR standards, HIPAA, PCI-DSS, and CCPA.
What’s more––ensure that any protocols your solution employs are up-to-date and comply with industry standards.
7. Deployment options
Deployment generally comes in two major forms:
- On-Premise: This deployment offers full control over your infrastructure, allowing you to customize security settings to meet specific needs. This is ideal for organizations with stringent security requirements and compliance obligations
- Cloud-Based: This deployment offers excellent scalability and accessibility, enabling remote access from any location with an internet connection. This is beneficial for remote staff and mobile device access.
Splashtop Enterprise offers both the popular cloud-based solution hosted on AWS and an on-premise solution.
With that out of the way, let’s dive more specifically into Splashtop.
Overview of Splashtop’s Security Features
Although we are dedicated to making RealVNC the most secure remote access software on the market, Splashtop is seen by many as a safe choice for both personal devices and remote computer management for businesses. It’s amongst the most popular solutions for remote access software, and that is unlikely to happen if security concerns were widespread.
The company’s flagship product for remote access, Splashtop Business Access, comes with a series of security features and protocols aimed at keeping data safe:
- Splashtop uses 256-bit AES Encryption to secure the file transfer during remote sessions, ensuring that the information remains confidential and protected against unauthorized access.
- Furthermore, Splashtop employs TLS protocols, including TLS 1.2, to safeguard connections and make interception nearly impossible.
- Device authentication is mandatory, and users can opt for two-factor authentication to add an extra layer of security.
Many organizations, including Microsoft, Harvard, and even government agencies like the City of Milwaukee, use Splashtop Business Access. These are entities that place a premium on security, so their continued custom must come with a little reassurance for the rest of us.
Compliance with industry standards
Splashtop shows its dedication to security with compliance with a wide array of industry standards.
It adheres to:
- HIPAA Compliance (essential for healthcare professionals to safeguard patient information)
- GDPR Compliance (ensures the protection of user data privacy rights)
- SOC 2 Compliance (meets rigorous security and privacy standards)
- ISO/ IEC 27001 Compliance
Splashtop also supports PCI, FERPA, and CCPA. These compliances make it suitable for various sectors, including finance, education, and healthcare.
Previous Security Vulnerabilities
Even the most secure systems can encounter vulnerabilities, and Splashtop is no exception. In a world of bad actors, these vulnerabilities are often only brought to light when something happens.
Notably, two significant security incidents (both now resolved) highlight this problem with the modern IT environment:
- In 2020, CVE-2020-12431 revealed a Windows privilege change issue in Splashtop Software Updater versions before 1.5.6.16. Insecure permissions on configuration files and named pipes allowed local privilege escalation. This vulnerability, which affected Splashtop Streamer and Splashtop Business versions before 3.3.8.0, opened a sensitive gateway for malicious actors to hijack the system.
- More recently, CVE-2023-3181 identified a local privilege escalation vulnerability affecting Splashtop Software Updater for Windows versions 1.5.6.21 and prior. This exploit allowed authenticated local users to gain SYSTEM-level privileges by manipulating insecurely created temporary directories and files. The issue was severe, given how easy it was to exploit and the high potential impact.
Patches were quickly and effectively rolled out to address and close the mentioned problems.
In our opinion, Splashtop did well in quickly resolving these threats, taking them seriously and addressing them thoroughly and timeously.
Common attack vectors and risks for Splashtop and other Remote-Access Platforms
When you are considering implementing a remote access solution in your organization, it is important to understand the various attack vectors that can expose remote access software to malicious exploits. Many vulnerabilities come down to user error in some fashion, such as not maintaining strict security policies.
Common attack vectors include:
- Weak Passwords. If users do not implement strong, complex passwords or multi-factor authentication, unauthorized access can be a huge risk for both personal devices and each account your company manages.
- Unpatched Software. Cyber attackers often exploit unpatched software vulnerabilities like CVE-2020-12431 and CVE-2023-3181. Regular updates are critical, but they can sometimes lag behind threat vectors.
- Insecure Network Configuration. Even with solid encryption protocols like AES-256 and TLS, poor network configurations, such as exposed endpoints and a lack of firewall protection, can leave users vulnerable to intercepts and your file transfer exposed.
All in all,if good network discipline is maintained across your company in mitigating these attack vectors, we are confident Splashtop’s security features should be adequate in most cases.
That being said, to mitigate risks of these attack vectors even further, you might instead choose to make use of RealVNC‘s end-to-end security measures which include mandatory encryption, perfect forward secrecy, identity checking, and other key features such as automatic blacklisting or session permissions.
How an Alternative to Splashtop Compares: RealVNC
In our opinion, when seeking a secure remote access solution, it’s essential to consider all factors, including encryption, deployment flexibility, and data protection.
That’s why RealVNC is often considered to be the most secure remote access solution on the market, offering several advanced features that strengthen your organization’s security and user control.
Here’s what makes RealVNC truly stand out among its competitors:
1. Advanced security features
- RealVNC employs top-of-the-line encryption protocols, including AES-256 encryption, to safeguard data during remote sessions.
- It allows administrators to define permissions for users who remotely access the system. This means you can control which devices and files each user can access.
- Regular security assessments ensure that RealVNC’s infrastructure remains safe against evolving threats.
2. Deployment flexibility
You can choose between on-premises and cloud-based solutions based on your specific needs. Whether you need strong control through on-premises installations or the flexibility of cloud-based access, they can support your needs.
3. Data protection focus
- RealVNC offers detailed logs of remote sessions, which means your IT department has easy access to the data needed to spot threats and conduct security assessments. They can review session histories to monitor activities and ensure compliance.
- Comprehensive audit trails can trace user actions and system events, aiding in the identification and resolution of security issues.
- RealVNC facilitates secure file exchanges during remote sessions by keeping data encrypted and protected.
Three Top Secure Remote Access Practices
Choosing the right remote support tool is just half the battle. The other half consists of creating a secure environment to protect your organization’s data.
Here are some best practices to follow:
- Encourage everyone to use strong, unique passwords. A strong password includes a mix of letters, numbers, and special characters. Add an extra layer of security by enabling 2FA.
- Regularly check your systems for security weaknesses. Use security scanning tools to identify areas that might be vulnerable to attacks. Once you find security issues, fix them right away with software updates or by changing security settings to close any gaps.
- Teach employees about security best practices, like how to recognize phishing emails and the importance of using secure connections. Well-informed staff are less likely to make mistakes that could lead to security breaches.
Your Security Partner Shouldn't Just Safeguard Data. It Should Be Proactive in Mitigating Risks.
So, back to the question: Is Splashtop safe? As mentioned above, we feel it meets many of the security requirements businesses might have, but does that make it the best remote access solution on the market? It depends.
- Splashtop employs strong security measures and doesn’t have a history of breaches in the volume or magnitude of many of its competitors, such as TeamViewer, for example.
- It is also one of the popular solutions, and that rarely happens to service providers who are lax in their security duties.
That being said, as part of our commitment to providing the world’s most secure remote access solution,RealVNC is proactive in keeping up with security standards, addressing user feedback, and adding new functionalities that do more than just enhance security measures.
Try RealVNC for free and let us know your feedback. We’re always here to listen to what you have to say. Experience the RealVNC difference for yourself.






