Walk into a room of system administrators and ask whether they prefer SSH or VNC, and you’re bound to get some strong opinions. Some swear by the precision of the command line, while others will never give up the convenience of having a full remote desktop session. The debate over VNC vs SSH is as old as system administration itself, because each protocol offers something the other cannot.
Remote access is, of course, the foundation of modern IT operations. Administrators rarely sit in front of racks of servers and manage hosts from KVM consoles. They must connect across a network to troubleshoot, deploy, and monitor remote systems. This task typically means either running commands in a text shell (SSH) or controlling the entire desktop environment on another server (VNC). Like with most things in IT, which approach works best depends on the situation, the workload, and what operating system the host machine is running.
This article won’t settle the VNC vs SSH debate, but it will explain the differences between the two and why both are still needed more than ever. You’ll see how each method supports enterprise workflow, what security measures apply, and where performance factors can influence adoption. We’ll also highlight how the most advanced adaptation of the VNC protocol, RealVNC Connect, provides secure remote access software out of the box for enterprises.
How VNC Works: Remote Desktop Access
Virtual Network Computing (VNC) is one of the earliest and most widely adopted remote desktop technologies. The principle behind how it works is simple enough: a VNC server captures a computer’s screen output, compresses it into data packets, and sends that information to a client across the network. The client receives the packets, then displays the graphical environment, creating the experience of sitting directly in front of the remote system.
The Remote Framebuffer (FRB) protocol is the underlying standard behind VNC. RFB is responsible for transmitting pixel information, encoding the graphical updates, and interpreting the mouse strokes, clicks, and keyboard input from the client user. When a user moves their mouse or types on a keyboard, those actions are forwarded back to the VNC server, which then executes them on the target machine.
Since we’re talking about a bidirectional interactive session of a complete desktop here, encoding efficiency matters. Early implementations of VNC transmitted raw pixel data and required high bandwidth. Modern versions employ compression algorithms to reduce traffic while still maintaining a high-resolution image on the client side. Some VNC implementations can even leverage your GPU to handle heavy applications and high-resolution displays.
VNC is most commonly used on Windows servers and desktops, but because it works at the framebuffer level, it is cross-platform by design. A VNC server running on Linux and macOS can also be accessed by nearly any client that supports the protocol. This flexibility allows IT teams to connect to a variety of systems without relying on platform-specific solutions like Microsoft’s RDP.
For organizations that use VNC but require enterprise-grade security, RealVNC Connect provides hardened authentication and cross-platform support that extends well beyond what the standard open-source VNC options provide.
How SSH Works: Secure Command Line Access
Secure Shell Host (SSH) delivers encrypted command-line access to remote systems with extremely low overhead (even over a 56k dial-up connection) and strong session integrity. Administrators use SSH to open a terminal on a target server, authenticate, and execute commands as if sitting right in front of it. The protocol separates concerns into a transport layer, an authentication layer, and a connection layer to maintain reliable communication, even over untrusted networks.
The transport layer phase negotiates algorithms and establishes confidentiality. Modern SSH stacks tend to favor Curve25519 key exchange, Ed25519 host keys, and AEAD ciphers like chacha20 or AES-GCM. Older RSA and classic Diffie-Hellman groups are still around, though modern admins prefer newer options for security posture.
Once the channel is protected, user authentication proceeds with public keys, short-lived certificates, or tightly-scoped passwords. The connection later then kicks in with allocation of virtual channels for shells, exec requests, or port forwarding.
A typical workflow using SSH looks like this:
- The client uses a terminal or terminal emulator like Putty, where they establish the connection either via CLI command SSH user@host:port or by entering the hostname or IP of the target server (as is the case with apps like Putty).
- The server provides a shell such as bash, zsh, or fish.
- Operators run system utilities, read logs with journalctl or tail, modify configuration, and log outcomes to change records.
On Linux, the OS most associated with SSH, this approach scales across thousands of nodes because text operations are inherently fast and scriptable.
For those who dread CLI-only administration, don’t fret. The feature depth of SSH can extend beyond a plain terminal with X11 forwarding. While users might be disappointed to learn you can’t forward an entire desktop, X11 over SSH will allow a single remote application from the host machine to be displayed on the local computer.
SSH tunneling can also be used to securely encapsulate traffic from other applications (including VNC), and administrators can use SCP to transfer files bidirectionally between host and client.
VNC vs SSH: What Are the Key Differences in Remote Access?
Since SSH works universally with almost every operating system (yes, even Windows) and VNC is cross-platform, the choice between the two comes down to how administrators prefer to interact with a remote system. VNC offers a full desktop experience where the client receives a mirror image of the host’s desktop. SSH delivers a text-only command line interface that’s efficient, but it means you need to know your stuff to use it.
The major dividing line between the two comes down to performance. A VNC host transmits continuous screen updates across the network, which requires much more bandwidth. SSH moves only text and control signals, which keeps latency extremely low, even across slow connections like satellite and cellular.
Security is another big dividing factor. SSH is encrypted out of the box and benefits from proven cryptographic standards. Early and even some modern open-source VNC solutions aren’t encrypted at all, or require a bit of configuration to get encryption working. Some users even tunnel their VNC connections through SSH, really driving home how secure and versatile SSH actually is.
Modern enterprise-grade VNC implementations like RealVNC Connect provide session encryption, modern authentication, and compliance support verified through independent audits.
Below are the main differences between VNC and SSH at a glance:
| Aspect | VNC (Remote Desktop) | SSG (Command Line) |
| Interface | Full graphical desktop | Text-only shell |
| Performance | Higher bandwidth and heavier system load | Low bandwidth and lightweight communication |
| Security | Varies by implementation | Encrypted by default |
| Use Cases | GUI apps, training, user support, and troubleshooting | Automation, scripting, and log analysis |
To this day, both protocols remain central to remote access strategies, and most administrators deploy them side by side to manage every type of remote server effectively. VNC is chosen when administrators need full interactive control beyond basic functions, including GUI applications, user assistance, and multi-step troubleshooting. SSH is preferred for precise, scriptable tasks such as config changes, package management, log review, file transfers, and automation.
Security Considerations: Protecting Remote Systems
Unfortunately, remote access invites risk, especially on public-facing servers. Because of this, remote administration of access solutions demands a strong focus on security. Both SSH and VNC face threats if not deployed without safeguards, but best practices and enterprise features can close most of the gaps.
SSH Security Risks and Mitigations
With SSH, encrypted communication is prioritized. However, exposed servers are frequent targets for attack. Common issues and responses are:
- Malicious actors use scanners like Nmap to detect open SSH ports (TCP:22). Administrators can configure the SSH server to listen on a different port or require local access via a VPN.
- Logins that are password-based are vulnerable to brute-force attacks. It’s best to use SSH keys, protected by passphrases, and disable password authentication entirely.
- Root login via SSH is particularly vulnerable if credentials are stolen. Teams typically disable root SSH login completely and favor privilege escalation with sudo or a separate admin account.
- Brute force scripted attacks can overwhelm servers and create a lot of noise. Tools like fail2ban monitor SSH logs and block offending IP addresses after multiple failures.
- Man-in-the-middle attacks are mitigated by verifying host key fingerprints before trust establishment. This functionality is a core component of modern SSH.
VNC Security Risks and Mitigations
Older versions of VNC had some notable security concerns because the base protocol lacked encryption. Modern versions offer encryption and can be made more secure by:
- Enabling encryption on VNC applications that support it. Otherwise, the data and even passwords are sent in plain text. If encryption isn’t available, tunneling VNC traffic through SSH forwarding provides an encrypted transport.
- Simple password authentication can be guessed or stolen. Platforms like RealVNC Connect offer modern authentication standards and can be integrated with enterprise SSO.
- Just like SSH, the native VNC port (TCP:5900+N) exposes the service to scanners. Moving the listening port or hiding it behind NAT and firewalls reduces the risk.
- Sessional hijacking risks are also addressed by encrypting data in transit with modern encryption standards.
Compliance frameworks like PCI-DSS and ISO 27001 require organizations to demonstrate that their remote systems are secure. Reviewing OWASP secure authentication guidance is recommended before deploying any remote access tool.
RealVNC Connect: The Modern Approach to VNC Security
For enterprises that demand standardization for VNC, RealVNC Connect security controls address all the common risks and compliance needs:
- Full-session encryption and modern authentication (MFA, SSO) for secure communication with granular permissions and client approval prompts.
- Certified to ISO 27001:2022 and Cyber Essentials and supports GDPR, CCPA, HIPAA, PCI-DSS, and EU NIS2.
- No session recording by default and no access to in-session data. The remote system privacy features include Privacy Mode, screen blanking, and input lock.
- RealVNC-owned infrastructure for brokering, with a 24×7 SOC, code signing on all binaries, and regular white-box audits plus independent penetration tests.
- Centralized management, MSI and Group Policy deployment, brute-force protection, and detailed log and audit trails that are accessible in the portal or via the dedicated API.
Performance and Resource Requirements
The protocol you choose to provide remote access has a direct effect on performance, resource usage, and the end-user experience. The way each technology handles network traffic and system load explains why administrators often rely on both, but in different contexts.
SSH Performance Factors and Tuning
SSH is legendary for operating well under the most trying network conditions. Since only text and control data move across the link, the protocol doesn’t need a lot of bandwidth. Needless to say, SSH doesn’t need a lot of performance tuning, but typical practices include:
- Keep-alive and sign-of-life signals sent in the session can keep an open connection stable in cases where the host has not received active traffic for some time.
- Compression flags such as SSH -C improve throughput when transferring logs or other heavy data.
VNC Performance Factors and Tuning
VNC streams a graphical desktop as a continuous image, so naturally it consumes bandwidth. Applications with heavy visual changes and high refresh rates, like streaming video or 3D rendering, increase this traffic even further. Optimization for VNC performance includes:
- Compression algorithms like those used by RealVNC Connect reduce the amount of pixel data being transmitted and use advanced encoding techniques that automatically adapt to bandwidth.
- Local GPU acceleration offloads some of the screen capture encoding, lowering the CPU rate while keeping frame rates up.
- Quality settings can be adjusted to turn off unnecessary desktop components, such as the desktop background and animation effects.
- Scaling features that translate low-resolution host desktops to high-resolution or multiple monitors help keep images clear.
Practical Use Cases: When to Use SSH, VNC, or Both
The choice between VNC and SSH depends on the task at hand. Each protocol addresses specific needs, and administrators often tend to use them both together for more complete coverage.
VNC: Graphical Administration and Support
A VNC server provides full visual screensharing, which makes it ideal for:
- Managing Windows and non-core Windows Server tools or dashboards that don’t have a CLI equivalent.
- Running development environments, such as IDEs that need a GUI
- Supporting remote users by viewing what their desktop looks like so you can solve their issues in real time.
- Operating graphical applications like CAD and web-based panels.
SSH: Command Line Efficiency
Administrators use SSH when they want quick, efficient control over a remote server. It works best for:
- Reviewing system logs and running monitoring commands
- Scripting deployments across hundreds of servers at once
- Remotely accessing servers that are headless (not running a GUI at all)
- Configuring cloud notes and container clusters remotely
Integration and Complementary Usage
We’ve spoken a lot about forwarding and tunneling VNC sessions through SSH connections in this guide. Many administrators do this when dealing with older or open-source VNC applications residing on Linux servers and desktops.
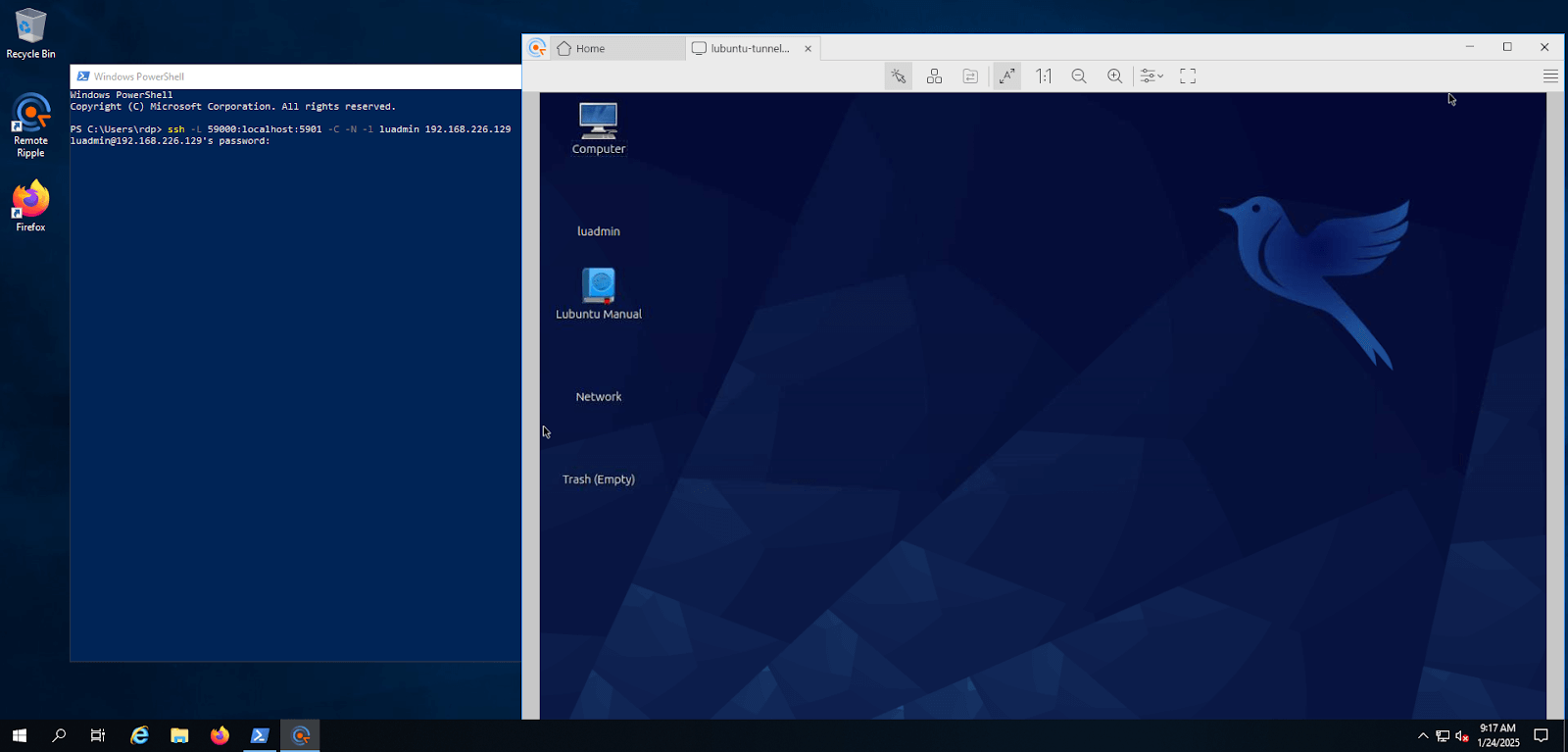
How to Tunnel a VNC Session Through SSH
A secure tunnel can be created with a simple SSH command. The process begins by choosing the local port that the client will connect to. Port 5901 is a common choice, but any unused port will work.
- Open a local terminal window (this can be done on a Windows Server with OpenSSH installed).
- Run the following command, replacing user with your account name and server with the hostname or IP of the remote server:
SSH -L 5901:localhost:5901 user@server
- Keep the session open. This command forwards the VNC traffic received on local port 5901 via SSH to the same port on the remote host.
- Start the VNC client and connect it to localhost:5901. Now the communication between the client and the VNC server is encrypted inside the SSH channel.
This configuration lets administrators protect VNC traffic with strong encryption and authentication while retaining the full graphical control you need.
While this works well, it’s not ideal for unattended sessions and really doesn’t work well at scale. RealVNC Connect delivers a fully encrypted VNC session that eliminates the need for SSH forwarding and tunneling for Linux, reducing complexity while maintaining enterprise efficiency and security.
Hybrid Workflows: Combining the Strengths of Both
There are times when you might actually need both at the same time. For example, a Windows Server acting as a jump box into a locked-down network subnet, where you then launch an SSH session to servers located on that subnet.
On Windows Server, OpenSSH is also now integrated and installable. This means administrators can launch PowerShell sessions over SSH, combining familiar Windows scripting with the encrypted transport that SSH provides while using VNC or RDP.
Cross-Platform Remote Server Support
One thing that both VNC and SSH have in common is their cross-platform support. A single client can connect to almost any system. It’s this functionality that makes both VNC and SSH ideal for administrators dealing with mixed environments.
VNC Coverage
A VNC server can run on Windows, Linux, or macOS, providing full desktop access regardless of the host operating system. Modern implementations like RealVNC Connect can extend this support to mobile operating systems like Android and iOS, meaning administrators can connect to a Windows or Linux server using just their smartphone.
SSH Coverage
SSH, too, is nearly universal. Most Unix-based platforms, routers, and appliances include an SSH client by default, and as we’ve already stated, Microsoft has integrated OpenSSH directly into Windows.
Administrators can now launch PowerShell or CMD sessions through SSH, making it easier to manage heterogeneous environments even if you’re running a near-full Windows shop.
RealVNC’s VNC Technology Leadership
RealVNC Connect knows VNC. After all, we invented it. Our platform has played a defining role in advancing the VNC protocol from its origins at AT&T Labs to today’s enterprise-ready deployments. RealVNC’s solutions extend beyond basic remote desktop access, combining secure design with enterprise-grade features.
Key leadership areas include:
- Protocol development: The founding work on the original VNC server architecture and ongoing contributions to open standards.
- Security certifications: Independent audits, compliance with frameworks, and support for Zero Trust strategies.
- Performance improvements: Advanced encoding algorithms that reduce bandwidth and keep applications responsive, even over poor network conditions.
- Enterprise integrations: Compatibility with identity systems, including SSO, PAM, and MFA.
- Reliability at scale: Support for large deployments, clustering, and high-availability configurations.
- Professional services: Consultation, training, and long-term support that help IT teams deploy and run remote access securely and efficiently.
Enterprise demand continues to grow for flexible yet hardened tools. RealVNC Connect for enterprise provides these capabilities to organizations looking to go beyond SSH and RDP for their remote access needs.
Decision Framework for Choosing VNC vs SSH
Selecting between VNC and SSH depends more on context than on a single “best choice.” IT decision-makers need to weigh:
- Task type: GUI-driven applications need VNC. There’s no skirting around that. If you perform more text operations and automations, especially in Linux environments, SSH is ideal.
- User skill: Less experienced ITSD staff may prefer graphical workflows over CLI. However, advanced users tend to benefit more from using the command line.
- Security requirements: SSH is encrypted by default. VNC requires enterprise implementations like RealVNC Connect to provide truly secure remote access.
- Network quality: SSH excels on poor links, but if you have staff in the field who need desktop troubleshooting, SSH won’t help. A VNC remote access solution is more ideal here.
In most enterprises, a combination of both builds resilient workflows for almost every remote server scenario. RealVNC Connect supports this dual model by delivering secure adoption across platforms.
Conclusion: Strategic Technology Selection
The choice between SSH and VNC highlights two complementary approaches to modern remote access. SSH offers a lightweight and encrypted option for command-line administration, while VNC delivers a full graphical desktop experience for interactions with GUI-driven applications.
Most enterprises will benefit from deploying both and matching each protocol to specific tasks and user skill sets.
If your organization is leaning more toward VNC, RealVNC Connect provides enterprise-grade solutions, no SSH tunneling required. Contact RealVNC today. Our expert consultants will help design a secure deployment that aligns with your infrastructure and operational requirements.
Frequently Asked Questions
Can VNC and SSH be used together?
Yes. Administrators establish SSH tunnels with port forwarding to transmit VNC server sessions through encrypted traffic. The combination of graphical remote access with strong key-based authentication through this system provides enhanced security.
Which protocol is better for system administration?
It depends on the task. SSH provides the best solution for running scripts, automating tasks, and reviewing logs on distant servers. VNC is the best option for GUI-driven applications and remote desktop assistance for users.
Which option is more secure by default?
All communication is encrypted automatically through SSH. RealVNC Connect enterprise software enhances the base VNC protocol with encryption, MFA, and auditing features, making graphical sessions equally secure for regulated environments.