There’s no doubt that securing your workforce’s remote work process is a must for minimizing cyber risks. But to do that, you’ll need to learn more about RDP vs. VPN to make an informed decision.
Here’s what we’ll cover:
- An overview of RDP vs. VPN
- When to use a RDP or a VPN connection
- Pros and cons of each remote access method
- Other alternatives to consider for an even more secure connection
What is Remote Access?
Remote access allows you to connect to a computer or network from any location. It’s crucial for tasks like remote support, managing servers, or accessing files from a remote office. Essentially, it allows remote workers to connect to any given network (like a corporate network) as if they’re on-site, no matter where they are. For example, an IT administrator can use remote access to fix a server issue in a data center miles away.
An overview of remote access
A remote network access session usually runs via a secure internet connection. It lets users interact with a system as if they were physically present. This flexibility means employees can work from virtually anywhere, whether at home, in a café, or on the road, as long as they have a stable internet connection.
And while remote desktop access is convenient, it can pose security risks if not properly managed. Unsecured remote connections can become entry points for cyberattacks, therefore strong security measures to prevent unauthorized access (like RDP and VPN) have become essential tools.
Still, each has unique benefits and potential vulnerabilities. For instance, while RDP offers a direct connection to a computer, a VPN server provides network-wide access, which requires careful setup to avoid security pitfalls like unauthorized access.
Importance of remote access for businesses
For businesses, remote access is vital. It supports remote work, allowing their employees to access company resources, applications, and files from anywhere. Plus, it can boost productivity and flexibility.
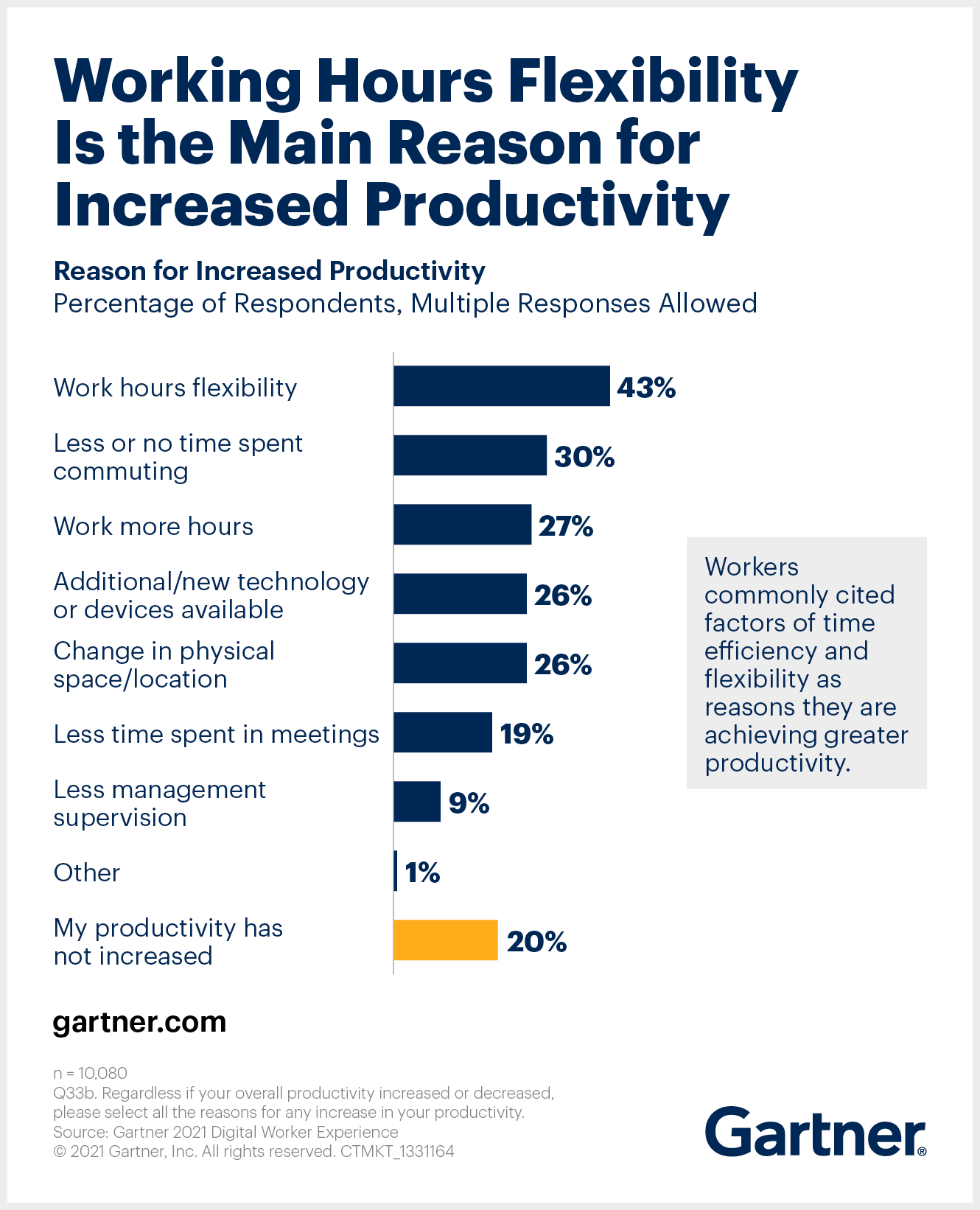
How so? Gartner suggests that employees who benefit from work hours flexibility and less or no time commuting experience a productivity increase. Moreover, workplace flexibility is a key factor in any benefits package, and everyone is on the hunt for jobs allowing remote working. Offering such capability means you can attract top talent globally without the constraints of geographical boundaries.
How about those experiencing a decrease in productivity? The same study highlights that this situation is caused by connectivity issues and technology changes, which means that companies investing in the right stack, resources, and tech hardware will contribute to better productivity levels for their employees.
Could remote working be the key to a healthy and steady workforce? It seems like it. Besides, remote access reduces overhead costs. In fact, businesses save an average of $11,000 annually per remote worker by cutting expenses related to physical office spaces.
Brief overview of remote access solutions
There are different ways to establish a secure remote access session. Each solution has its own strengths and weaknesses, and they include:
- Remote Desktop Protocol (RDP) – Developed by Microsoft, RDP allows users to remotely control another computer. It provides a graphical interface to interact with a remote machine as if they were sitting in front of it.
- Virtual Private Network (VPN) – VPNs create a secure, encrypted connection to a network over the internet. This allows users to access the network as if they were on-site. For instance, employees can use a VPN to access their company’s internal network while working from home.
- Virtual Network Computing (VNC) – VNC is a cross-platform technology that facilitates remote access and control over a network. Unlike RDP, VNC is more focused on sharing the screen and inputs, so it’s usually used for collaborative work or remote troubleshooting.
- Cloud-based Virtual Desktops – Services like Amazon WorkSpaces and Microsoft Azure Virtual Desktop provide cloud-hosted desktops that users can access remotely. These virtual desktops run in the cloud, allowing access from various devices without requiring direct control of a physical machine.
- Remote Access Software – Tools like RealVNC Connect offer remote desktop software access for all types of purposes. RealVNC Connect comes with extensive features like file transfer, remote printing, and multi-platform support, alongside security protocols like encrypted access, multi-factor authentication, and industry certifications like ISO/IEC 27001:2013, GDPR, CCPA, HIPAA, and PCI-DSS.
- SSH (Secure Shell) – Commonly used for accessing servers, SSH allows secure command-line access to remote systems. It’s widely used in Linux environments for system administration tasks.
- Zero Trust Network Access (ZTNA) – Offers a more modern approach by granting access based on strict identity verification, reducing the risk of unauthorized access.
Understanding Remote Desktop Protocol (RDP)

RDP (Remote Desktop Protocol), is a proprietary secure network communication protocol developed by Microsoft. It allows users to connect to and control a remote computer as though they were physically present at the machine. A RDP connection uses port 3389 and offers a graphical interface, so it’s an intuitive choice to access remote desktops.
Benefits of RDP
RDP offers a high level of control and flexibility for remote access. You can manage a remote computer with full administrative privileges, which makes it one of the top remote access methods for system administrators.
Need to install software or modify system settings on an off-site server? RDP makes it as straightforward as if you were on-site. It’s also relatively easy to set up. Windows users can activate the RDP feature in a few clicks, creating an immediate remote access solution without additional software.
RDP Security Risks and Vulnerabilities
RDP comes with security risks if not properly configured. Open RDP ports can become easy targets for hackers, often leading to brute force attacks where attackers attempt to guess the login credentials. poorly secured RDP setups can also serve as a gateway for malware, which cyber attackers can use to install malicious software.
To mitigate these risks, it’s crucial to use strong, unique passwords and turn on multi-factor authentication. Administrators should also consider using RDP gateways and network-level authentication to limit exposure. Without these measures, RDP will slow down network performance due to its resource-intensive nature and become a security liability.
PS: For businesses needing a secure and flexible alternative, RealVNC offers encrypted remote access solutions that combine control like the one offered by RDP with top security features. Get started for free.
Understanding Virtual Private Network (VPN)

A Virtual Private Network (VPN) extends a private network across a public network, like the internet. By creating a secure, encrypted “tunnel” between the user’s device and the network, a VPN allows safe access to resources on a private network as if the user were physically on-site. For instance, remote employees can use a VPN to access their company’s internal network from anywhere.
Benefits of VPNs for Secure Remote Access
VPNs are widely used for their high level of security and encryption. They encrypt internet traffic, which makes it difficult for hackers to intercept sensitive data like login credentials or confidential files. VPNs also offer flexibility, as employees can connect securely from remote locations.
Setting up a VPN is generally straightforward, with many operating systems and routers offering built-in VPN support. For businesses, this means a scalable solution that can be deployed quickly to support remote work.
VPN Security Features and Benefits
VPNs use end-to-end encryption to secure data transmissions, so that even if data is intercepted, it remains unreadable. They work with protocols like OpenVPN or IPsec to establish secure connections.
Besides encryption, VPNs offer secure authentication methods, such as multi-factor authentication (MFA), to verify the identity of a remote user. Advanced VPN services can also include additional security features like malware protection and intrusion detection.
And while VPNs provide some level of security, they can have limitations, especially if not paired with other measures. For example, a VPN does not inherently protect the remote device from malware or unauthorized access, not does it offer access control for different remote devices.
For a more comprehensive approach to secure remote access that combines encryption with tailored user controls and real-time monitoring, remote work access software like RealVNC Connect is the better choice.
Key Differences Between RDP vs. VPN
So, what makes a VPN vs. a RDP solution different? And how can these technologies empower your remote workforce to perform their duties from a local network, their own home, or even another continent? Let’s get into all of it.
Flexibility and accessibility
- RDP allows a user to take full control of the remote system’s desktop environment. It transmits the keyboard and mouse inputs from the client to the host computer, while the host sends back the graphical user interface to the client. This interaction is done over TCP port 3389, with additional support for UDP if enabled.
- VPNs, in contrast, provide a more network-oriented form of remote access. By creating an encrypted tunnel between the remote user and the internal network, VPNs allow access to network resources, like file servers, databases, or internal websites, without granting control over any specific machine.
Security capabilities and encryption
- VPNs generally provide stronger encryption and security than RDP connections. Most VPNs use AES-256 encryption, the gold standard for securing data transmission. VPNs use RSA keys for secure key exchanges and protocols like IKEv2/IPsec and OpenVPN. Still, a 2023 IBM Security Report indicates VPNs aren’t foolproof. Misconfigurations, outdated software, and vulnerabilities like CVE-2019-14899 have caused data breaches.
- An RDP connection, meanwhile, uses up to 128-bit RC4 encryption, significantly weaker than VPNs’ 256-bit AES. RDP is more susceptible to brute-force and man-in-the-middle (MITM) attacks. However, RDP has its risks, as proved by vulnerabilities like BlueKeep (CVE-2019-0708). While patches and recommended practices have been released, they require an experienced IT team to implement.
Ease of use and implementation
All tools and technologies facilitating third party connections RDP are relatively straightforward to set up.
- For small-scale deployments, enabling RDP on the target machine and allowing port 3389 through the firewall can suffice. However, this simplicity comes at the expense of security if not properly managed. Organizations must use Remote Desktop Gateway or Virtual Private Network (VPN) tunneling to encapsulate RDP traffic and secure RDP deployments.
- Setting up a VPN requires configuring a VPN server, installing client software, and setting up appropriate routing and firewall rules. For large-scale enterprises, this involves deploying VPN concentrators and managing a Public Key Infrastructure (PKI) to handle digital certificates for authentication. Modern VPN solutions also support Zero Trust Network Access (ZTNA) principles, which restrict users to remotely access resources based thorough verification.
Our verdict: VPN or RDP?
- RDP is optimal for specific use cases requiring direct system control, such as IT troubleshooting or accessing high-performance workstations remotely. However, due to its inherent security vulnerabilities, it should always be deployed with additional security measures.
- VPNs provide a more holistic approach to secure remote network access. They are preferable for organizations prioritizing data security, compliance, and access to diverse network resources. However, VPNs require a more intricate setup and maintenance process.
Both VPN and RDP are good remote server access solutions to consider. However, VNC Connect combines the security features of VPNs with the ease of RDP, offering a secure, encrypted remote access solution that integrates with your existing infrastructure.
How to Choose the Best Remote Access Solution
- Ensure the solution uses strong encryption standards like AES-256 and supports multi-factor authentication (MFA).
- Choose a solution that supports your operating system (Windows, macOS, Linux) and provides solid remote network access with no downtime, from any location.Consider long-term costs, including licensing, maintenance, and scalability. RDP may be more cost-effective for small businesses needing access to a single machine. For larger businesses, VPNs allow employees to easily access secure networks remotely and so the are more scalable.
Get the Remote Access Software That Ticks the Boxes
Choosing between RDP and VPN comes down to your business’s unique needs. RDP gives you direct control and flexibility, so it’s a solid chocie for general support tasks, but it requires careful security management. On the other hand, a VPN solution can provide secure, encrypted network access, which making it great for broader remote work scenarios.
Remember, there’s no such thing as a one-size-fits-all solution. When deciding on VPN vs RDP your solution, focus on key factors: security and encryption, flexibility, ease of use, and scalability. Ask yourself: Does this solution fit into my current setup, tech stack, and organizational culture? Can it grow with my business?
With the right remote access solution, you’re empowering each remote user in your team to work securely and efficiently from anywhere.
Our final take for businesses selecting a remote access solution
If you’re looking for a solution that balances security, ease of use, and flexibility, consider RealVNC Connect. It offers secure remote access without the hassle of complex setups.
With RealVNC, you get a balanced blend of control and encryption, so that your team can work effectively from any location. Whether it’s secure remote support or accessing your office network, RealVNC Connect ticks all the right boxes. Try it for free.